Posts By Brian Pickering
Abstract: Small and medium enterprises (SMEs) make up a significant part of European economies. They are often described as poorly place to deal with cyber risks though because of resource constraints or commercial interests. Providing appropriate tooling would facilitate a greater appreciation of the risks and provide mitigation strategies. In a series of workshops demonstrating visualization tools for cybersecurity, constructs from healthcare models such as awareness, self-efficacy, and a willingness to engage were investigated to throw light on the likelihood that the technologies would be adopted. Although most constructs were validated, it turns out that self-efficacy could more appropriately be interpreted as a desire to understand a broader company narrative rather than empowering any individual to identify and manage cyber risk. As part of an ongoing examination of technology acceptance, this work provides further evidence that technology must be contextualized to make sense for the individual as part of the SME rather than as individual employee.
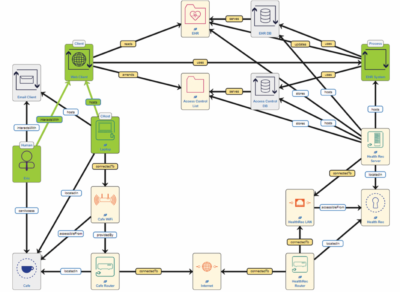
Abstract: Small and medium-sized enterprises (SMEs) rarely conduct a thorough cyber-risk assessment and they may face various internal issues when attempting to set up cyber-risk strategies. In this work, we apply a user journey approach to model human behaviour and visually map SMEs’ practices and threats, along with a visualisation of the socio-technical actor network, targeted specifically at the risks highlighted in the user journey. By using a combination of cybersecurity-related visualisations, our goals are: i) to raise awareness about cybersecurity, and ii) to improve communication among IT personnel, security experts, and non-technical personnel. To achieve these goals, we combine two modelling languages: Customer Journey Modelling Language (CJML) is a visual language for modelling and visualisation of work processes in terms of user journeys. System Security Modeller (SSM) is an asset-based risk-analysis tool for socio-technical systems. By demonstrating the languages’ supplementary nature through a threat scenario and considering related theories, we believe that there is a sound basis to warrant further validation of CJML and SSM together to raise awareness and handle cyber threats in SMEs.
We’re all increasingly aware that criminals are exploiting the virtual environment in a variety of ways, sometimes tricking individuals to reveal sensitive information or holding their data literally to ransom. So, we’re all encouraged to go online with caution, to update software regularly, install virus scanners and firewalls, and to be suspicious of unsolicited items […]