Cyber Threat Intelligence and how is leveraged inside Cyberkit4SME – Part 2
25th May, 2023
Author Giampaolo Darelli
Formats and Protocols
STIX (Structured Threat Information eXchange) and TAXII (Trusted Automated eXchange of Indicator Information) are the main standards in the Cyber Threat Intelligence field; we can say that STIX states the “what” of threat intelligence, while TAXII defines “how” that information is transmitted.
Regarding STIX, the main purpose of the format is to represent a cyber threat in the most contextualized way possible; to achieve this goal the danger is represented as an edge-and-node-based graph data model, where the nodes are called STIX Data Objects (SDO) and the edges are called STIX Relationship Objects (SRO).
The SDOs represent information such as the Actor behind the threat, the techniques, tactics, and procedure, the indicators (IPs, hashes, domains, etc.) that the actor used, the vulnerability exploited, and so on.
The SROs, the edges, are meant to connect SDOs so that, over time, users will be able to develop in-depth knowledge of threat actors and their techniques.
Below is shown a representation of a “Campaign” object, which is basically a dictionary in JSON format that expresses details about a malicious campaign.
{
“type”: “campaign”,
“id”: “campaign–8e2e2d2b-17d4-4cbf-938f-98ee46b3cd3f”,
“spec_version”: “2.1”,
“created”: “2016-04-06T20:03:00.000Z”,
“modified”: “2016-04-06T20:03:23.000Z”,
“name”: “Green Group Attacks Against Finance”,
“description”: “Campaign by Green Group against targets in the financial services sector.”
}
The “Campaign” object, as stated above, can be in relation with other objects, below is a sample visual representation of a possible threat.

While STIX is used to represent the Cyber Threat, TAXII is used to share information about the threat.

The protocol has been created to standardize the exchange of CTI information and it works over http/https protocols; it defines a set of services and messages that when implemented allow various organizations to share information for the recognition, prevention, and mitigation of attacks.
The main service of a TAXII service is called “Collection” and is basically an interface to a server-provided repository of objects that allows a producer to serve consumers in a request-response flow.
High-Level Integration
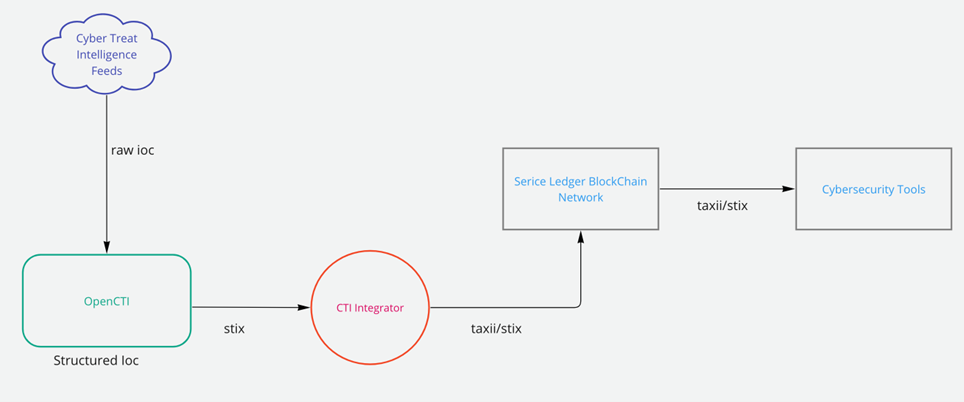
As stated in the previous blog post, in Cyberkit4SME OpenCTI is currently used as a collector of intelligence feeds; those feeds are structured and saved as STIX Objects in the platform, so that can be easily analyzed, enriched, and shared.
In order to integrate those feeds with the Service Ledger Sogei’s CERT provided a dynamic connector, called CTI Integrator, that fetches data from OpenCTI and, following various criteria, such as feed name or CTI date, transmits them to Service Ledger.
Below is high-level architecture of the integration: